Selfhosted
A place to share alternatives to popular online services that can be self-hosted without giving up privacy or locking you into a service you don't control.
Rules:
-
Be civil: we're here to support and learn from one another. Insults won't be tolerated. Flame wars are frowned upon.
-
No spam posting.
-
Posts have to be centered around self-hosting. There are other communities for discussing hardware or home computing. If it's not obvious why your post topic revolves around selfhosting, please include details to make it clear.
-
Don't duplicate the full text of your blog or github here. Just post the link for folks to click.
-
Submission headline should match the article title (don’t cherry-pick information from the title to fit your agenda).
-
No trolling.
Resources:
- selfh.st Newsletter and index of selfhosted software and apps
- awesome-selfhosted software
- awesome-sysadmin resources
- Self-Hosted Podcast from Jupiter Broadcasting
Any issues on the community? Report it using the report flag.
Questions? DM the mods!
view the rest of the comments
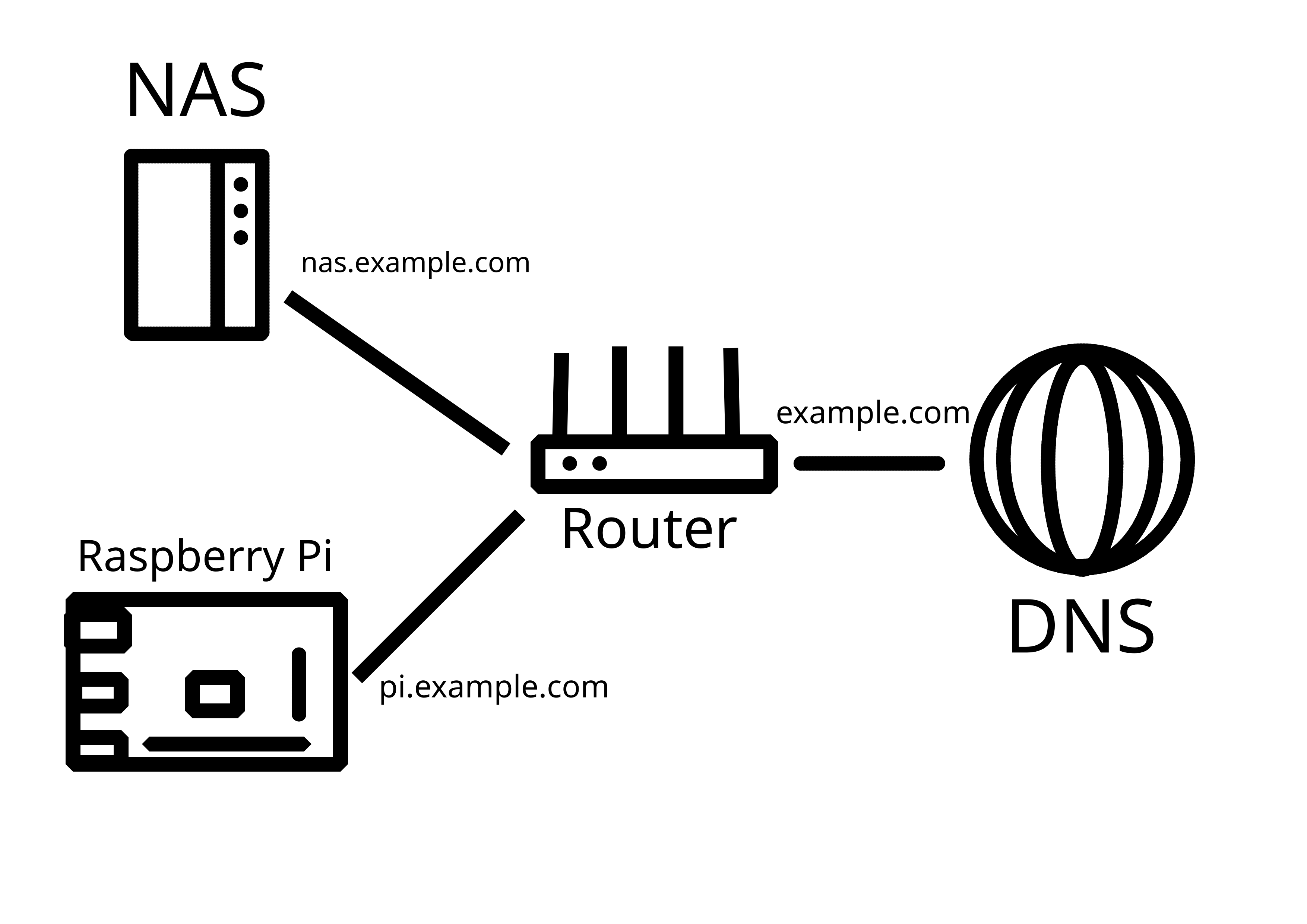
I have wrestled with the same thing as you and I think nginx reverse proxy and subdomains are reasonably good solution:
Only fault I’ve discovered are some public ledgers of TLS certs, where the certs given by letsencrypt spill out those semi-secret subdomains to the world. I seem to get very little to no bots knocking my services though so maybe those are not being scraped that much.
Pretty solid! Though insta-ban on everything :80/443 may backfire - too easy to just enter the domain name without subdomain by accident.
Could be indeed. Looking at the nginx logs, setting a permaban on trying to access /git and a couple of others might catch 99% of bots too. And ssh port ban trigger (using knockd for example) is also pretty powerful yet safe.