LG tvs and rokus I know for a fact don't have vpn apps available. And I'm sure there are plenty more.
Saik0Shinigami
Plex clearly scans your media collection and does upload the metadata and they can add more data collection any time they want.
No. The local metadata agent requests the data, it doesn't upload a list of what you have but requests the metadata it's missing. And you could say that a log collection of what data it retrieves is risky... except now they cram so much nonsense on the home page that all of that is fluff that would obfuscate that heavily...
But you can configure the meta-agent. You can not request it at all.
How are they going to scan a server on my network thats behind my firewall with nothing open to the internet?
So then you agree with my initial statement that I start with of "people need to implement it sensibly knowing the potential risks."?
If so... then why get into a hissy fit over this when my statement was clear? People shouldn't implement Jellyfin without understanding the risks... it's not innately secure and requires additional solutions to make it use-able. And thus, should be recommended only when that is disclosed.
Stick to plex if you want to run a free internet tv service for your cousin and their kids and whoever else and you aren’t concerned with their or your privacy.
What evidence of privacy problems do you have against Plex?
I've wiresharked, splunked, checked literally everything that I sent to Plex not all that long ago... Turns out it a whole fuckton of nothing and generic metadata pulled from the media agent. Turns out that as long as you turn off the dumb features, you're not sending all that much. It's much easier for me to tell people to turn that shit off than it is to convince them to install apps and configure everything.
I’m into self-hosting because data privacy is my primary concern.
Privacy won't matter if a major studio catches wind of this type of vulnerability and decides to start scanning for jellyfin instances. The subpoenas will come shortly after.
Tunnels have overhead. MTU overhead itself can cut 5% of your total bandwidth as a default (1500 -> 1420). Forget all the side-channel control stuff.
MTU itself is an interesting issue for wireguard. It defaults to 1420, which should be fine in most cases as the default is 1500 for most ISP connections. But there are interesting cases where you need to go less... If you try to cram a 1420 MTU packet down a 1440 MTU ISP connection (you need 28Bytes overhead minimum, so would need 1412 in Wireguard in this case)... you're rewriting a fuckton of packets and splitting tons of data that can ruin your connection speed (halving immediately).
I have seen some people recommend 1384 MTU before... The lower you tune this for compatibility the less speed you get.
Once again though... this is way over a normal users head. And likely even over yours since you don't seem to recognize that this is happening and that it isn't byte per byte the same.
You should expect wireguard to lose you 5% speed minimum... with other issues potentially making it worse.
Edit: clarification on a sentence cause the wording was bad.
And every time I speak up about it... I find users that never heard of it and want to learn how to reasonably fix it. And those discussion happen.
Example:
Am I a shill for talking about the risk of this specific software and even how to mitigate it with others? or am I a shill because you're defensive over software that you happen to use/like?
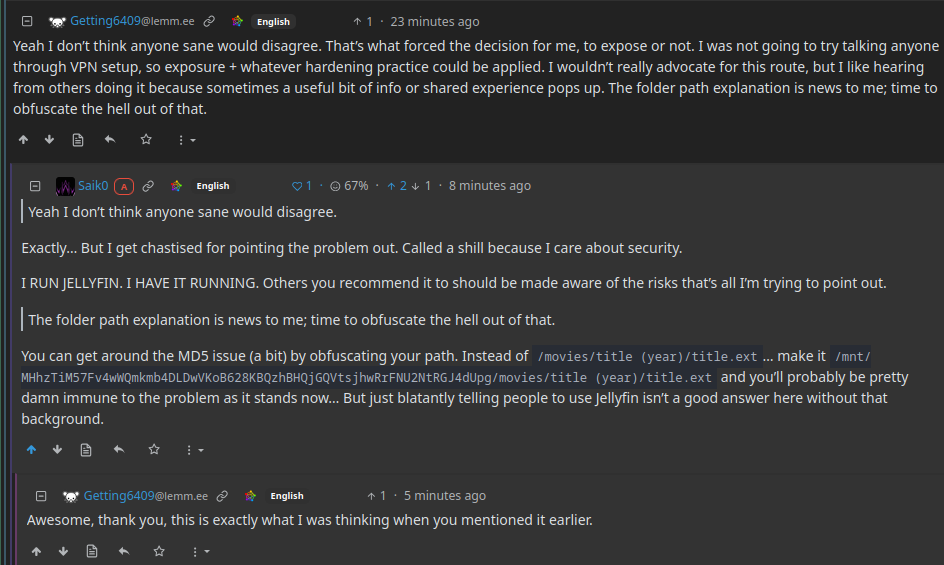
Yeah I don’t think anyone sane would disagree.
Exactly... But I get chastised for pointing the problem out. Called a shill because I care about security.
I RUN JELLYFIN. I HAVE IT RUNNING. Others you recommend it to should be made aware of the risks that's all I'm trying to point out.
The folder path explanation is news to me; time to obfuscate the hell out of that.
You can get around the MD5 issue (a bit) by obfuscating your path. Instead of /movies/title (year)/title.ext... make it /mnt/MHhzTiM57Fv4wWQmkmb4DLDwVKoB628KBQzhBHQjGQVtsjhwRrFNU2NtRGJ4dUpg/movies/title (year)/title.ext and you'll probably be pretty damn immune to the problem as it stands now... But just blatantly telling people to use Jellyfin isn't a good answer here without that background.
Awesome... cool for you. The average person doesn't even understand or even know what a VPN is.
I taught undergrad and grad college level IT courses. Many students there didn't even understand what a VPN actually is.
Edit: It works for you... great... it could even work for many... Awesome. There are legit use cases for the majority that VPN just doesn't work.
and everyone but a single user just hears the ocean.
I'm sorry, but this made me bust laughing. This is dead accurate for a few people in my life.
Then I have to troubleshoot and tell them to toggle it off and on again…
And this is exactly the type of support a lot of people just don't want to do (including me). And the options really boil down to settle for supporting all this, or the risk of public access to unauthenticated endpoints.
They could just fix the endpoints and it'll be a non-issue. But they won't because "backwards compatibility".
There are even other options that I can pre-emptively offer... but they all SUCK.
You can whitelist ip access... ISP ips rotate and are dynamic.
You can setup crowdsec and/or fail2ban... until a user fails to login a few times in a row because users are users and get themselves banned, now you're back to support role.
VPNs already covered ad nauseam.
There are options... they all suck, especially when the answer of JUST FIX THE ENDPOINT is sitting right there.
And I'm talking about the reverse problem. That you would need to expose it in order for it to work with other users... OTHERWISE be on the hook to support users via VPN + Jellyfin, or in the case of TV apps, Router+VPN+Jellyfin. That doesn't scale up well the moment you have someone not in your house that uses your stuff. It doesn't have to be pirate TV. Could just be a kid at college.
It's not me that's the problem. I have a permanent tunnel back to my house/infrastructure (straight wireguard). It's communicating how to use it to my users that the problem... I already do enough support that I'm just not opening that can of worms to non-tech people.
Fair concern... But I can tell you unauthenticated endpoints aren't one. I haven't tested any others personally.
Just the same that we don't know if the jellyfin ones don't have further issues that people just haven't found yet. What's your point? One is known for 4+ years now and is a wontfix... the other is unknown and no evidence to suggest otherwise.