I use firewalld as generic firewall and fail2ban as IPS/anti-bruteforce solution (blocks IPs using firewalld's ipsets)
vegetaaaaaaa
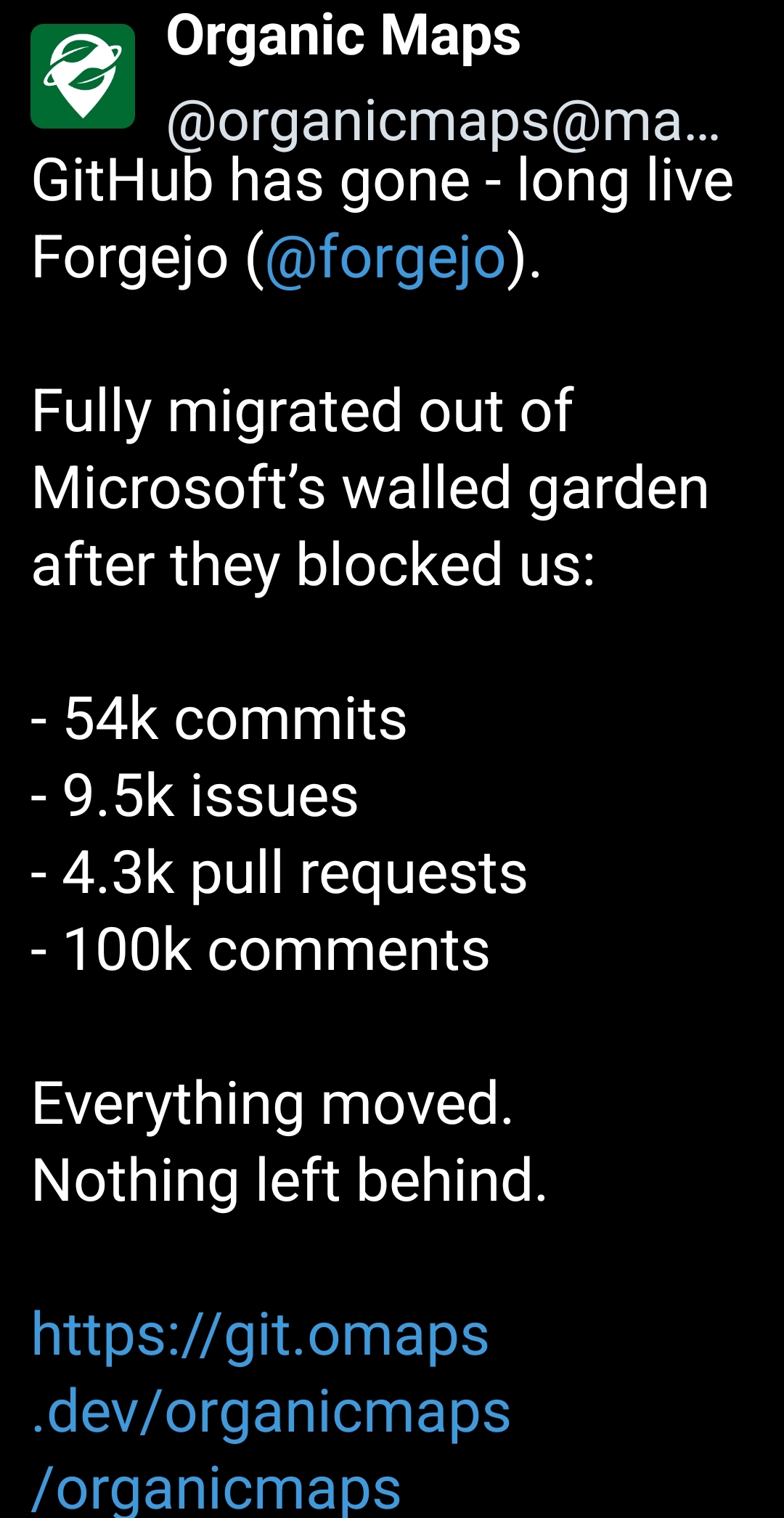
I have copied the latest git revision c67b943aa894b90103c4752ac430958886b996b2 from https://gitlab.tt-rss.org/tt-rss/tt-rss to my gitea instance which is mirrored to https://gitlab.com/nodiscc/tt-rss and https://github.com/nodiscc/tt-rss.
I don't intend to make changes or bugfixes (it's working fine), but I will try to keep it compatible with the PHP version in Debian stable, since I've been using it for years and would really like to keep doing so.
- Any of https://staticsitegenerators.bevry.me/
- Any webserver + virtualhost config that serves plain HTML pages
- a build/upload script
A full-blown samba domain is extremely overkill if you don't have a fleet of windows machines.
You can get centralized user management with a simple LDAP server or similar, no need for a domain.
Also, snapshots-based backups have limited uses (can't easily restore only a single file, eats quite a bit of storage). The only times where I actually needed backups were because I fucked up a single application or database, don't want to rollback the whole OS/data drive for that.
https://lemmy.world/post/34029848/18647964
- Hypervisor: Debian stable + libvirt or PVE if you need clustering/HA
- VMs: Debian stable
- podman if you need containerization below that
You can migrate VMs live between hosts (it's a bit more work if you pick libvirt, but the overhead/features or proxmox are sometimes overkill, libvirt is a bit more barebones, each has its uses), have a cluster-wide L2 network, use a machine as backup storage for others... use VM snapshots for rollback, etc. Regardless of containerization/orchestration below that, a full hypervisor is still nice to have.
I deploy my services directly to the VM or as podman containers in said VMs. I use ansible for all automation/provisioning (though there are still a few basic provisioning/management to bootstrap new VMs, if it works it works)
- Hypervisor: Debian stable + libvirt or PVE if you need clustering/HA
- VMs: Debian stable
- podman if you need containerization below that
I’m not sure of any formal name
Cloudflare turnstile
If you needs are simple, write a simple playbook using the proxmox ansible module https://docs.ansible.com/ansible/latest/collections/community/general/proxmox_kvm_module.html
Terraform/Opentofu provides more advanced stuff but then you have to worry about persistent state storage, the clunky DSL... used it when acsolutely needed, you can do 90% of this stuff with the proxmox ansible module.
If you need to make your playbook less verbose, move the logic to a role so that you can configure your VMs from a few lines in the playbook/host_vars. Mine looks like this (it's for libvirt and not proxmox, but the logic is the same)
# playbook.yml
- hosts: hypervisor.example.org
roles:
- libvirt
# host_vars/hypervisor.example.org.yml
libvirt_vms:
- name: vm1.example.org
xml_file: "{{ playbook_dir }}/data/libvirt/vm1.example.org.xml"
state: running
autostart: yes
- name: vm2.example.org
xml_file: "{{ playbook_dir }}/data/libvirt/vm2.example.org.xml"
autostart: no
- name: vm3.example.org
xml_file: "{{ playbook_dir }}/data/libvirt/vm3.example.org.xml"
autostart: no
- name: vm4.example.org
xml_file: "{{ playbook_dir }}/data/libvirt/vm4.example.org.xml"
autostart: no
disk_size: 100G
turn that monitor off and save power?
apache can do load balancing as well https://httpd.apache.org/docs/2.4/mod/mod_proxy_balancer.html
I'd pick something that you already use across your stack, to minimize the number of different integration/config styles/bugs...
unattended-upgrades doesn't do that unless you explicitly specify
Unattended-Upgrade::Automatic-Reboot "true";in the config. Check/usr/share/doc/unattended-upgrades/README.md.gzThe main configuration file is
/etc/apt/apt.conf.d/50unattended-upgrades, maybe you put your config in the wrong place?here is mine